In today’s data-driven digital landscape, protecting personal and business privacy has become a core concern for internet users. When we talk about private browsing, many people immediately think of Chrome’s Incognito mode. However, for professionals and digital marketers who need to manage multiple independent identities simultaneously, a more powerful and specialized tool - the fingerprint browser - is becoming an indispensable choice. This article delves into the fundamental differences between these two technologies, analyzes their working principles, and evaluates their applicability in different scenarios.
What is Chrome’s Incognito Mode?
Chrome’s Incognito mode is a basic privacy feature built into Google’s browser. Its core concept is relatively simple: after you close all windows, the browser clears your browsing history, cookies, and site data. Many mistakenly believe this is a completely anonymous way to browse, but this is a common misconception.
How Incognito Mode Works
Understanding the true working principle of Chrome’s Incognito mode helps debunk some common myths.
Session Isolation and Data Deletion: When you open an Incognito window, Chrome creates a separate, temporary “session.” Within this session:
- No Browsing History is Saved: The URLs you type into the address bar and the links you click are not recorded in the browser’s history.
- No Cookies or Site Data is Saved: Cookies set by websites to recognize you, as well as session data generated from logging in, are stored in this temporary space. When you close all Incognito windows, this space is deleted, and the website treats it as though you have logged out and left.
- No Form Data or Passwords are Saved: The information you fill out on web pages and any saved passwords are also not stored locally.
What It Doesn’t Do (Key Limitations):
- It Doesn’t Hide Your IP Address: Your real IP address is fully visible to the websites you visit, your Internet Service Provider (ISP), your company’s network administrator, or your school’s IT department. They know your geographical location and online activities.
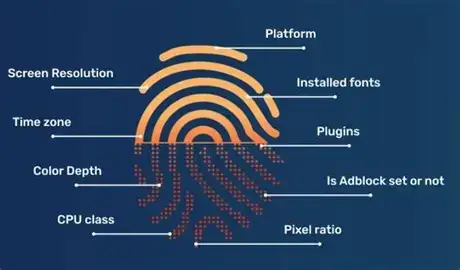
- It Doesn’t Isolate Your Device Fingerprint: This is the most overlooked aspect. Websites can “identify” you by collecting unique information from your device, even after you’ve cleared all cookies and cache. This information includes:
- Browser and OS information (User-Agent)
- Screen resolution and color depth
- List of installed fonts
- Browser plugins and extensions
- Hardware configuration (e.g., CPU cores, memory size)
- Canvas and WebGL rendering fingerprints: These are generated by drawing a specific pattern on a canvas and reading the result, making it nearly unique for every individual.
In simple terms, Incognito mode is like a “temporary room.” You can do things in this room that you don’t want other users (other people on the same computer) to know about. However, the landlord (website) and the doorman (ISP/network administrator) still know who (which IP address) entered the room, and they can also recognize you by your appearance (device fingerprint) in the crowd on the street.
What is a Fingerprint Browser?
A fingerprint browser is an advanced browser tool specifically designed for multi-account management and privacy protection. Unlike traditional private browsing modes, its core purpose is not to clear history after browsing, but rather to create a completely independent and isolated digital environment for each account during the browsing process, preventing platforms or websites from identifying and associating these accounts through technical means. It modifies and simulates the device’s “fingerprint” information, allowing each account to have a unique, untraceable identity in the digital world.
How Fingerprint Browsers Work
The design philosophy of a fingerprint browser is entirely different from Incognito mode. It’s not about “cleaning up afterward,” but about “disguising beforehand” and “permanent isolation.” It achieves this by creating multiple independent, differently-configured virtual browser environments.
Creating Isolated Profiles: The core of a fingerprint browser is the creation of multiple virtual “profiles.” Each profile is completely independent and has its own:
- Independent Cookie Cache: An account logged into one profile is invisible to all other profiles.
- Independent Browser Storage: Such as LocalStorage and IndexedDB.
- Independent Plugin and Extension Lists: You can install or not install specific plugins for each environment.
- Independent Proxy/IP (Optional): Each profile can be bound to a different proxy server, achieving IP address isolation.
Modifying or Fixing Device Fingerprints: This is the essence of a fingerprint browser. It allows users to view and even modify the “appearance” characteristics used to identify a device.
- Fingerprint Randomization: The most common method is to generate a new, plausible set of browser fingerprints each time the browser is opened, with random screen resolution, font lists, Canvas fingerprints, etc., making it difficult for websites to track.
- Fingerprint Spoofing/Cloning: Advanced users can “clone” the fingerprints of one profile to another or manually specify all fingerprint parameters. This allows two different accounts (using different profiles) to have identical digital identities, perfectly simulating the same person operating on the same device. This is the core requirement for scenarios like cross-border e-commerce and affiliate marketing.
Integration of Advanced Features:
- Proxy Integration: Seamlessly associate each profile with a different proxy IP, achieving dual isolation of IP and fingerprints.
- Automation Tools: Products like FlashID also integrate RPA (Robotic Process Automation) and window synchronization features to automatically execute tasks across multiple isolated accounts, greatly operational efficiency.
In simple terms, a fingerprint browser isn’t like a “temporary room,” but rather it’s like having a film props department with multiple stunt doubles for you. Each stunt double (profile) has its own identity (IP), appearance (device fingerprint), and memory (Cookie/data). You can send them to perform different tasks, and the outside world (website platforms) cannot tell that these doubles are actually being controlled by the same person, nor can they associate their actions together.
Key Differences in Their Working Principles
Understanding the mechanics behind each technology makes their differences crystal clear:
| Feature | Chrome Incognito Mode | Fingerprint Browser |
|---|---|---|
| Core Goal | Temporary privacy, preventing local data saving | Permanent identity isolation, preventing cross-account linking |
| Data Clearing | Automatic deletion after the session ends | Persistent storage in profiles, accessible anytime |
| IP Isolation | Not provided, uses real IP | Provided via independent IP binding per profile |
| Device Fingerprint | Not handled at all, uses real hardware/software fingerprint | Core feature, can be randomized, fixed, or cloned |
| Use Case | Personal temporary browsing, avoiding local traces | Business multi-account operations, evading platform detection |
| Nature | A “temporary, incomplete” privacy switch | A “powerful, proactive” identity management system |
Choosing the Right Tool for You
Scenarios for Using Chrome Incognito Mode
If you meet one or more of the following conditions, Chrome’s Incognito Mode will be sufficient for your needs:
- Temporary Information Query: Need to quickly search for a sensitive or private question, but don’t want these search records to remain in the local browser history.
- For example: querying medical symptoms, planning surprise gifts, browsing sensitive topics, etc.
- Using Public or Shared Computers: Logging in to personal accounts on shared computers in internet cafes, hotels, libraries, or offices, ensuring no login traces or data are left behind after you leave.
- For example: logging into personal email or social media, closing all windows after use, after which the data is cleared.
- Avoiding Leaving Local Traces: Not wanting others who share your device (such as family members, colleagues) to see websites you’ve recently visited or search content.
- Single Account, Short-term Login: Occasionally needing to log in to a non-important local account outside of your main browser for security reasons, without involving multi-account management.
- For example: logging into a forum that requires one-time verification, after which the account won’t be used again.
Key point: Incognito mode aims to solve the problem of “preventing personal data traces from being left on the same device.” It does not consider the risk of association with other devices or accounts.
Scenarios for Using Fingerprint Browsers
If your situation involves any of the following scenarios, then a professional fingerprint browser is a necessary and powerful tool:
- Multi-account, Multi-platform Parallel Operations: Need to manage multiple independent accounts simultaneously in one browser or device, with accounts that must achieve “zero correlation” with each other.
- For example: affiliate marketers operating dozens of Amazon/AliExpress/Shopify promotion accounts; e-commerce sellers managing stores on multiple different platforms.
- Evading Platform Risk Control and Detection: Need to prevent different platforms or websites (such as Facebook, Google, Amazon) from identifying multiple accounts as belonging to the same person through technical means (device fingerprint, browser fingerprint, IP address).
- Data Scraping and Automation: When conducting web scraping or using automation tools, you need to configure each crawling or operating thread with an independent browser environment to avoid being identified and banned by target websites.
- Cryptocurrency and Wallet Management: Need to securely manage multiple cryptocurrency wallets or exchange accounts in isolation to prevent account correlation and reduce asset risks.
- Ad Campaigns and A/B Testing: Need to test different ad creatives, landing pages in different browser environments, and ensure that the ad platform won’t identify multiple test accounts as the same advertiser.
- Professional-level Privacy Protection: Not just clearing local cache, but building one or more “virtual identities” isolated from real identity from the source (IP, browser fingerprint, Cookie).
Key point: Fingerprint browsers aim to solve the core problem of “simulating multiple independent, digitally uncorrelated identities on the same device.” It is an active, systematic account management solution.
Fingerprint Browser Applications and Advantages
Fingerprint browsers show significant value in several professional fields:
Affiliate Marketing: Affiliate marketers typically need to manage multiple promotion accounts to test different strategies or products. Fingerprint browsers ensure each account has a unique device environment and browser configuration, effectively avoiding detection by affiliate platforms.
Cross-border E-commerce: Platforms like Amazon and eBay have strict policies on account association. Fingerprint browsers can help sellers operate multiple stores securely, preventing platform bans due to identical device fingerprints.
Social Media Marketing: When managing multiple social media accounts, fingerprint browsers ensure each has a unique digital identity, avoiding detection by platforms as machine operations.
Web Scraping: Scrapers can use fingerprint browsers to disguise real device environments, reducing the risk of being banned by target websites and improving data collection stability and efficiency.
Cryptocurrency Operations: In cryptocurrency trading, fingerprint browsers can isolate different wallets and exchange accounts, enhancing account security and reducing association risks.
Introducing FlashID: A Professional Fingerprint Browser Solution
Among many fingerprint browser solutions, FlashID stands out with its powerful features and stability. FlashID is an integrated solution combining fingerprint browser and cloud phone technology, designed specifically for professional users who need to manage multiple accounts.
Core Advantages of FlashID
- Powerful Fingerprint Isolation Technology:FlashID creates unique browser fingerprints for each account, ensuring platforms cannot identify your different accounts through technical means.
- Cloud Phone Integration: Not only solves multi-account management for web browsers but also supports multi-account scenarios on Android mobile devices through cloud phone functionality, achieving full-platform coverage.
- Window Synchronization and RPA Automation: FlashID supports window synchronization and integrates RPA (Robotic Process Automation) technology to automate repetitive tasks, significantly improving work efficiency and saving labor costs.
- Wide Range of Applications: FlashID is suitable for multiple professional fields including affiliate marketing, cross-border e-commerce, digital marketing, social media marketing, web scraping, traffic monetization, and cryptocurrency.
- User-Friendly Interface: Even users without technical backgrounds can quickly get started and make full use of FlashID’s features.
How FlashID Solves Your Multi-account Management Challenges
Whether you need to manage 10 or 100 online accounts, FlashID provides a stable and reliable solution. Its advanced fingerprint isolation technology ensures each account has an independent digital identity, completely solving account association problems. Meanwhile, through automated window synchronization and RPA features, you can efficiently manage multiple accounts without spending a lot of time on repetitive operations.
For cross-border e-commerce sellers, FlashID can help you securely manage multiple Amazon or eBay stores, avoiding platform bans due to identical devices or browser environments. For affiliate marketers, FlashID allows you to test multiple promotion strategies simultaneously, increasing conversion rates and revenue.
Frequently Asked Questions (FAQ)
What’s the difference between a fingerprint browser and a VPN?
Fingerprint browsers primarily solve identity isolation at the browser level, while VPNs mainly hide your IP address. Both can be used together but address different dimensions of privacy.
Is using a fingerprint browser illegal?
In most countries and regions, using a fingerprint browser itself is not illegal as long as your activities comply with local laws. It’s primarily a technical tool, and how it’s used depends on the user’s intent.
Is Chrome’s Incognito mode really secure?
Chrome’s Incognito mode prevents local data saving but doesn’t protect your data from being seen by your ISP, employer, or visited websites. It’s also not completely anonymous.
Why do I need to pay for a fingerprint browser?
Free fingerprint browsers often have limited functionality or security risks. Paid fingerprint browsers like FlashID offer more stable performance, more powerful features, and better customer support.
Can fingerprint browsers prevent all types of tracking?
While fingerprint browsers significantly reduce tracking risks, no tool can provide 100% privacy protection. Advanced tracking technologies may attempt to bypass these protections.
Does FlashID support mobile devices?
Yes, FlashID provides cloud phone functionality supporting multi-account management on Android systems, addressing multi-account scenarios on mobile devices.
Will using a fingerprint browser affect website performance?
High-quality fingerprint browsers like FlashID are optimized to have minimal impact on website performance. However, complex fingerprint configurations might slightly increase page loading times.
How can I ensure my account security?
In addition to using a fingerprint browser, you should use strong passwords for each account and enable two-factor authentication, and regularly check account activity logs.
Are fingerprint browsers suitable for individual users?
While primarily aimed at professional users, individuals who need high levels of privacy protection can also benefit from fingerprint browsers.
Does FlashID offer a free trial?
Yes, FlashID typically offers a free trial period for users to experience its core features before purchasing.
You May Also Like


